Protect your company from vulnerabilities like Log4Shell.
A severe vulnerability in a widely used open-source library for Java recently shook the global IT landscape.
Log4Shell, a zero-day vulnerability affecting the popular Apache package, was made public on December 9, 2021 (CVE-2021-44228).
The vulnerabilty allows remote code execution (RCE) by submitting a specially crafted request, which enables attackers to take control of devices or computers on the internet that are running certain versions of Log4j.
The Apache Software Foundation, which publishes the Log4j 2 library, gave the vulnerability a CVSS score of 10 out of 10, which represents the strongest severity.
AXS Guard disposes of many features like SecureDNS, ReaQta Endpoint Security en IPS (Intrusion Prevention system) which can detect and protect your organization from these types of vulnerabilities.
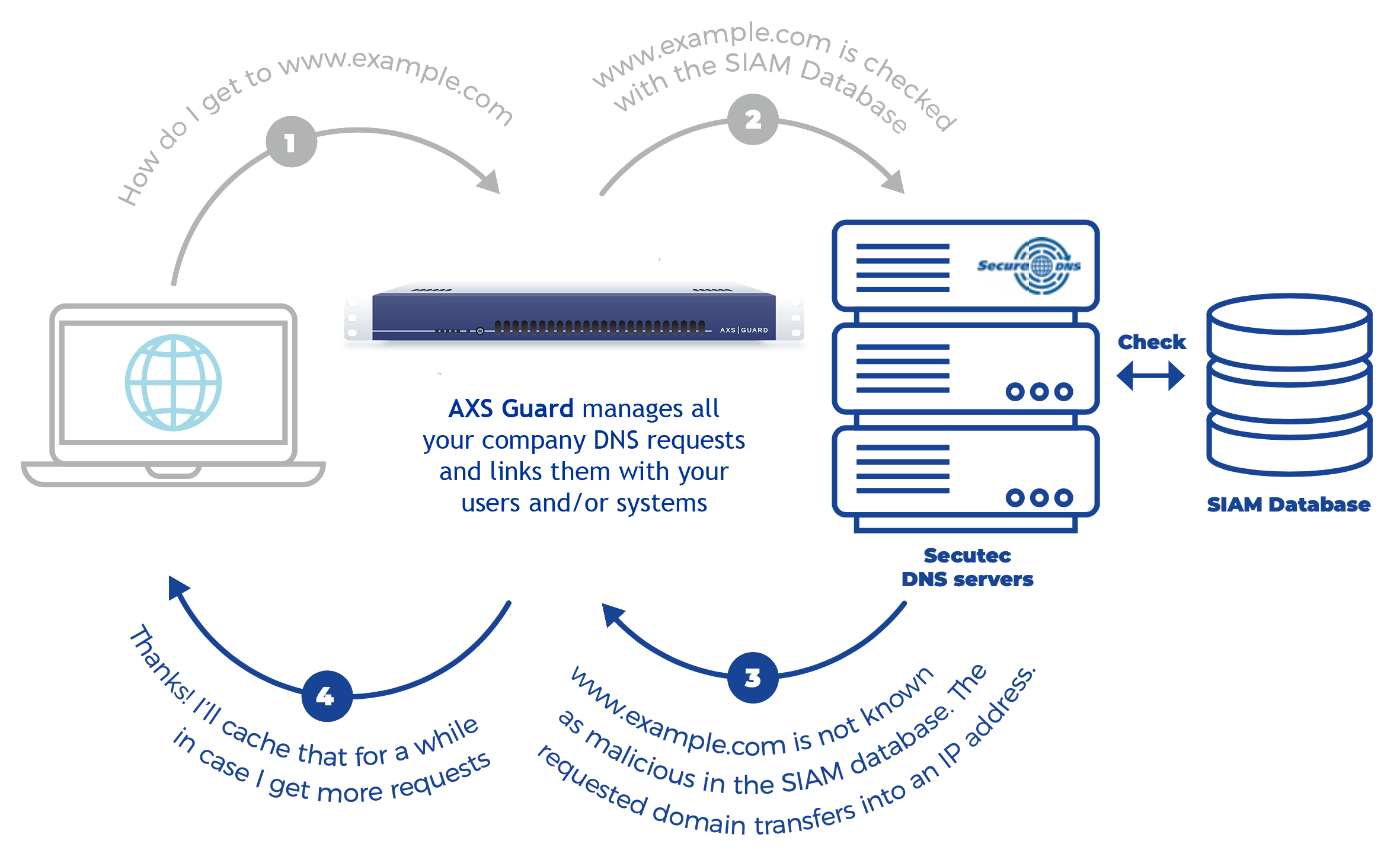
SecureDNS
AXS Guard integrated SecureDNS into the Premium Threat Protection Pack.
AXS Guard’s SecureDNS allows DNS requests to be checked against special databases to quickly identify suspicious and malicious domains.
Attackers and malware often leverage DNS because it is a trusted protocol used to publish information that is critical to networking clients.
Vulnerabilities such as Log4shell are no different in that respect. When the Log4j application is attacked, it will force the target to make a callback to a certain URL. An attacker can then use that URL to pass Base64-encoded commands to be executed on the vulnerable device.
As the domains and IP addresses in these callback URLs are malicious, they are immediately recognized and blocked by SecureDNS, causing the attack to fail.Note that we still recommend that you install the patches against this vulnerability so your network environment remains fully protected.
REAQTA - ENDPOINT SECURITY
AXS Guard's Endpoint Security solution is based on artificial intelligence developed by ReaQta.
It provides full infrastructure visibility, real-time endpoint monitoring and includes advanced data mining capabilities to discover dormant threats, such as Log4Shell.
The Log4Shell vulnerability leverages the Log4j Java Naming and Directory Interface (JNDI) to initiate a request to a malicious server that is controlled by an attacker.
The widespread use of Log4j in applications, combined with the simplicity of the exploit, allows for large-scale attacks across the Internet. While the exploit itself is simple to execute, additional post-exploitation activity is required for an attacker to establish a foothold on targeted networks.
AXS Guard’s AI-Driven Endpoint Security - powered by ReaQta, will provide visibility into unexpected behavior of any application that is leveraging Log4j, and will automatically detect and block any unusual activity which occurs during the post-exploitation phase of an attack.
More info about ReaQta Endpoint Security »

IPS - INTRUSION PREVENTION SYSTEM
The AXS Guard Intrusion Prevention System (IPS) is a preemptive approach to network security.
The IPS identifies potential software exploits and takes immediate action against them. The actions to be taken are based on existing preprocessors and a set of dynamic rules divided in classes.
To protect your network from this vulnerability at the IPS level, log in to your AXS Guard appliance and simply enable the Log4j rules in the ‘server-other’ class.


How to protect your business from Log4shell vulnerabilities?