
It is fair to think that hackers primarily penetrate through suspicious links in e-mails or other communication channels. Since those channels are often well protected, hackers keep finding other ways. For example, they more often revert to using USB ports as access to systems. We have listed here some suggestions on how to prevent this.
USB ports as access to your organization
Through an infected USB device, such as memory stick or external hard drive, hackers can install malware or malicious software (unnoticed). The concept is simple and potentially very damaging.
The big challenge with these attacks, of course, is the physical aspect involved. Unlike an online attack, this involves physically connecting a USB device to a system. In practice, this usually involves the use of "social engineering". For example, one will intentionally leave a USB flash drive in a public place. The intention is that the person who 'accidentally' finds it will naturally connect it to his/her computer or laptop out of curiosity (and ignorance).
LitterDrifter - A 'good' example of hacking via USB
The USB worm called LitterDrifter (so named by CheckPoint Research) is being used by Russian cyber-espionage services to target Ukrainian entities, among others. The worm has also been detected in countries other than Ukraine, including the United States, Vietnam, Chile, Poland, Germany and Hong Kong.
The malware has two goals:
- Spread itself across systems/drives in the network.
- Establish a channel to Gamaredon's command and control (C2) infrastructure (C&C servers are often hosted on Telegram channels).
How can you prevent this?
It makes sense to say "don't use (unknown) USB devices" or shut off access to USB." And if you use it, you should always have the "zerotrust" mindset, you know?
Unfortunately, of course, this is not realistic in practice. Therefore, you need to strengthen physical security with DNS security on the one hand and Endpoint security on the other.
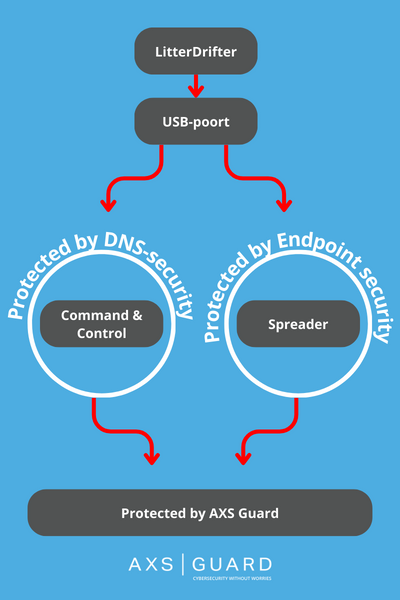
DNS-security
LitterDrifter's first objective, which is to establish a connection to the Command & Control Center (of Gamaredon), can be stopped by DNS security.
The Domain Name System (DNS) acts as a kind of "phone book" of the Internet, translating domain names into IP addresses, allowing computers to connect to appropriate Web sites and services.
DNS security involves filtering all DNS requests to block access to malicious websites, phishing sites or content that may be considered unwanted or dangerous. In this case, Gamaredon's servers are blacklisted so no connection can be made.
DNS-Security is a component of the AXS Guard Premium Threat Protection Pack.
Endpoint security
LitterDrifter's other function is to spread itself across a network to other systems on that network.
This danger can only be stopped by an adequate and modern Endpoint Detection & Response or EDR.
EDR is an advanced security technology that focuses on detecting, investigating and responding to cyber threats on endpoints, such as computers, laptops, mobile devices and servers within a network.
The key components of EDR are:
- Endpoint Detection: EDR software continuously monitors endpoints looking for suspicious activity, unusual processes or behaviors that may indicate a possible breach.
- Endpoint Response:Once a threat is detected, EDR provides the ability to respond immediately by taking actions such as isolating the affected device, stopping malicious processes or taking other corrective measures.
- Forensic capabilities: EDR software provides in-depth forensic capabilities by providing detailed information on the nature of the attack, endpoint involvement, and other relevant data needed for further analysis and response.
- Endpoint Visibility: It provides deep visibility into the activity of each endpoint within a network, enabling security teams to identify and understand suspicious activity.
- Behavioral Analysis: EDR solutions often use behavioral analysis and machine learning algorithms, in order to understand normal behavior of users and systems and identify suspicious activities based on deviations from this normal behavior.
EDR is a very important part of organizations' cybersecurity infrastructure because it enables organizations to respond to incidents quickly and accurately, reducing the impact of cyber attacks and strengthening endpoint security.
AXS Guard has integrated EDR in the form of Qradar EDR, a powerful solution provided by IBM.
Conclusion
The article highlights the growing threat of hackers using USB ports as an entry point for attacks on systems. In doing so, they can install malware on a device such as a USB flash drive, which is potentially dangerous to organizations. An example of this approach is the "LitterDrifter," a spy worm designed by Gamaredon, which allowed them to access Ukrainian systems.
To prevent this, in addition to physical security techniques such as avoiding unknown USB devices, it is recommended that advanced security measures such as DNS security and Endpoint Detection & Response (EDR) be used. DNS security prevents systems from connecting to malicious Web sites or attackers' command and control infrastructure. EDR provides in-depth protection by detecting, investigating and responding to suspicious activity on endpoints, allowing organizations to respond quickly to cyber threats.
The combination of DNS security and EDR, as integrated in solutions such as the AXS Guard Premium Threat Protection Pack, with IBM's Qradar EDR, is an essential part of organizations' cybersecurity and minimizes the impact of potential attacks via USB ports.
Other questions? contact!

USB as entry point for hackers