
In light of recent revelations regarding the cybersecurity breach at limburg.net , it's crucial to underscore the significance of securing Remote Desktop environments.
What are the details? Medusa's criminal hackers gained unauthorized access to limburg.net on November 17, 2023, through their publicly accessible RDP server. According to an expert consulted by Het Belang van Limburg, login credentials for this server were discovered online, allegedly belonging to an employee associated with Limburg.net
RDP is al lang gekend als een belangrijke zogenaamde “attack vector” voor hackers. Ook ITDaily publiceerde hierover enkele jaren geleden reeds een artikel (“‘Remote Desktop (RDP) is de motor achter tal van aanvallen").
Understanding the Vulnerabilities of the Remote Desktop Protocol (RDP)
While RDP itself isn't inherently unsafe, numerous installations are notorious for their susceptibility to hacking. Several factors contribute to this vulnerability:
- Lack of Multi-factor Authentication (MFA)
- Susceptibility to Brute Force Attacks
- Lack of Strict Encryption: Inadequate encryption practices in RDP deployments can pave the way for Man-in-the-Middle (MitM) attacks.
- Multiple Open External Ports: Any RDP server accessible from the internet requires open ports in the firewall, providing potential entry points for attackers. The presence of multiple open external ports increases the attack surface and exposes the RDP service to a higher risk of exploitation.
RDG: Enhancing Remote Desktop Security
The Remote Desktop Gateway (RDG) protocol rectifies some of the shortcomings associated with traditional RDP deployments through:
- Centralization: RDG consolidates access to multiple servers into a single, centralized point, streamlining management and enhancing control over remote connections.
- Centralized Management: With RDG, administrators gain centralized management capabilities, simplifying the administration of remote access policies and user permissions.
- Encrypted Traffic: RDG encapsulates RDP traffic within a secure HTTPS connection, bolstering security by encrypting data transmission between clients and servers.
While RDG represents an improvement over conventional RDP setups, it's important to note that it's not a panacea for all security concerns. At AXS Guard, we offer three comprehensive solutions designed to streamline and fortify your security infrastructure.
Best Practices for Securely Using RDP
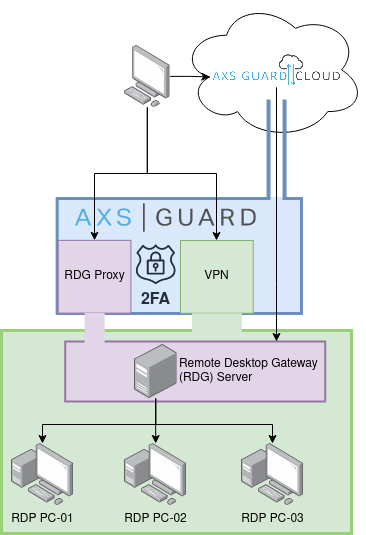
1. VPN
You can certainly utilize a VPN connection, secured with 2FA.
However, this approach may be excessive for your intended goals. After all, granting VPN access may inadvertently expose users to other segments of your network and introduce other hurdles.
- Users will be exposed to multiple authentication schemes.
- Your RDG server is no longer publicly accessible.
- Users will need to complete multiple logins.
- Achieving optimal security may necessitate a more intricate configuration involving firewall settings, authentication policies, and VPN configuration.


2. AXS Guard Enhanced RDG
The AXS Guard Enterprise Edition offers an enhanced Remote Desktop Gateway (RDG) solution with an application firewall, also known as Reverse Proxy, which is deployed in front of your RDG server. This extra layer enhances security and authentication for accessing the RDG server.
Using an "auto-learning" mechanism, AXS Guard securely stores login credentials for the RDG server. Upon authentication with AXS Guard, users are seamlessly logged into the underlying server without the need for additional manual login steps.
Introducing this additional layer provides numerous benefits:
- The layer acts as an extra barrier between the internet and the actual RDG proxy, ensuring that users do not directly interact with the RDG proxy, thereby bolstering security.
- Users will be exposed to multiple authentication schemes.
- Comprehensive Logging
- Single Sign-On (SSO) Support
- Custom Password Policies
- Automatic Login.
- Brute Force Protection
Additionally, AXS Guard offers a user-friendly application designed to facilitate secure RDP connections. With just one SSO application, users can authenticate against the AXS Guard RDG reverse proxy and the RDG server, simplifying the setup process and enhancing overall usability.
3. AXS Guard Remote Workspace
AXS Guard Remote Workspace provides a convenient method to access and control your desktop directly from your web browser.
- Effortless Desktop Access
- Utilizes multiple layers of encryption
- Users will be exposed to multiple authentication schemes.
- Single Sign-On (SSO) Support
- Effortless Connection Sharing
- Principle of Least Privilege: granting user access only to the resources they require.
- Mobile Device Support
- Printer and Component Compatibility
Conclusion
The recent breach at limburg.net through Remote Desktop underscores the susceptibility of RDP environments to cyber attacks. While the RDP protocol itself is not inherently unsafe, many installations remain vulnerable due to insufficient security measures, such as the absence of multi-factor authentication and encryption. Although a Remote Desktop Gateway (RDG) offers some improvements, it is not a comprehensive solution.
AXS Guard provides a range of solutions to address these vulnerabilities. From VPN with 2FA to Enhanced RDG with an application firewall, and Remote Workspace for convenient and secure access, AXS Guard offers robust security features. These solutions include multi-factor authentication, single sign-on support, brute force protection, and adherence to the principle of least privilege. Moreover, AXS Guard simplifies the setup of secure RDP connections with its user-friendly application.
Sources & References
ITDaily: https://itdaily.be/blogs/security/remote-desktop-rdp-is-de-motor-achter-tal-van-aanvallen/
Het Belang van Limburg: https://www.hbvl.be/cnt/dmf20240129_97245362
RDG Reverse Proxy Setup: https://documentation.axsguard.com/revproxy/?h=#rdg-servers
Remote Workspace https://documentation.axsguard.com/remote_workspace
For further inquiries, please contact support@axsguard.com (Enterprise bundle required).
Additional information about the Remote Desktop Gateway client: AXS Guard RDP Client

Securing Remote Desktop: Mitigating the Risk of Hacking